What Cloud Monitors Provides
- Centralized security monitoring across AWS and Azure environments - Direct integration with AWS Security Hub and Azure Defender - AI-powered remediation suggestions for security findings - Severity-based finding prioritization (Critical, High, Medium, Low, Info) - Search and filtering by resource type, region, and severity - Real-time security posture tracking with progress monitoring over time
Cloud Security Integration
Cloud Monitors leverages your existing cloud security tools to provide comprehensive monitoring:Supported Security Tools
AWS Security Hub: Centralized security findings from AWS services and
third-party tools
Azure Defender: Microsoft’s cloud security posture management and threat
protection
Cloud Monitors requires that AWS Security Hub (for AWS accounts) or Azure Defender (for Azure
accounts) be enabled and configured in your cloud environment. These services must be active to
pull security findings.
Getting Started
Step 1: Connect Your Cloud Account
Before running security scans, you need to connect your AWS or Azure account to Cloudgeni and ensure the appropriate security services are enabled.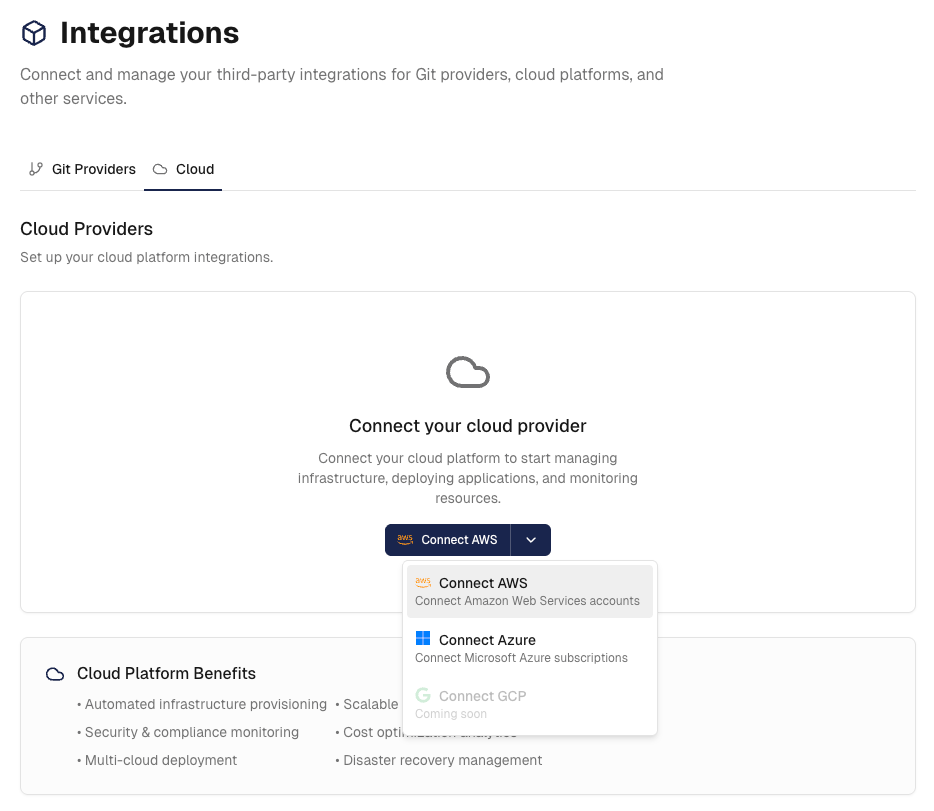
- Navigate to
Settings→Integrations→Cloudin your Cloudgeni dashboard - Select the cloud provider you want to connect to and follow the quick setup procedure
- Important: Ensure AWS Security Hub (for AWS) or Azure Defender (for Azure) is enabled in your cloud environment
Cloud Monitors pulls security findings from your existing cloud security tools. Cloudgeni requires
read-only access to your cloud resources and will never alter anything in your cloud environment!
Step 2: Run Your First Security Scan
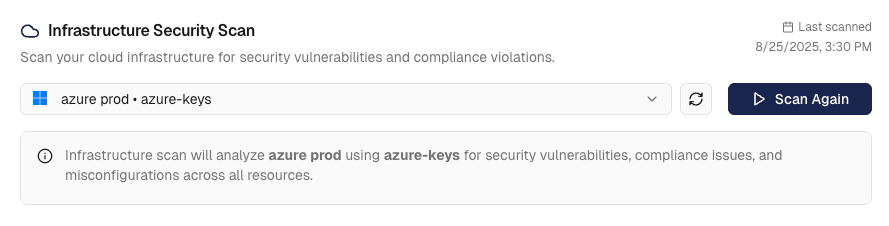
- Navigate to
Compliance→Cloud Monitorsand select your cloud account - With your cloud account selected, click “Scan” to start the security analysis
- The system will pull the latest security findings from AWS Security Hub or Azure Defender (this usually takes a few seconds)
Understanding the Security Dashboard
Once your scan completes, you’ll see a comprehensive security dashboard with your cloud security findings: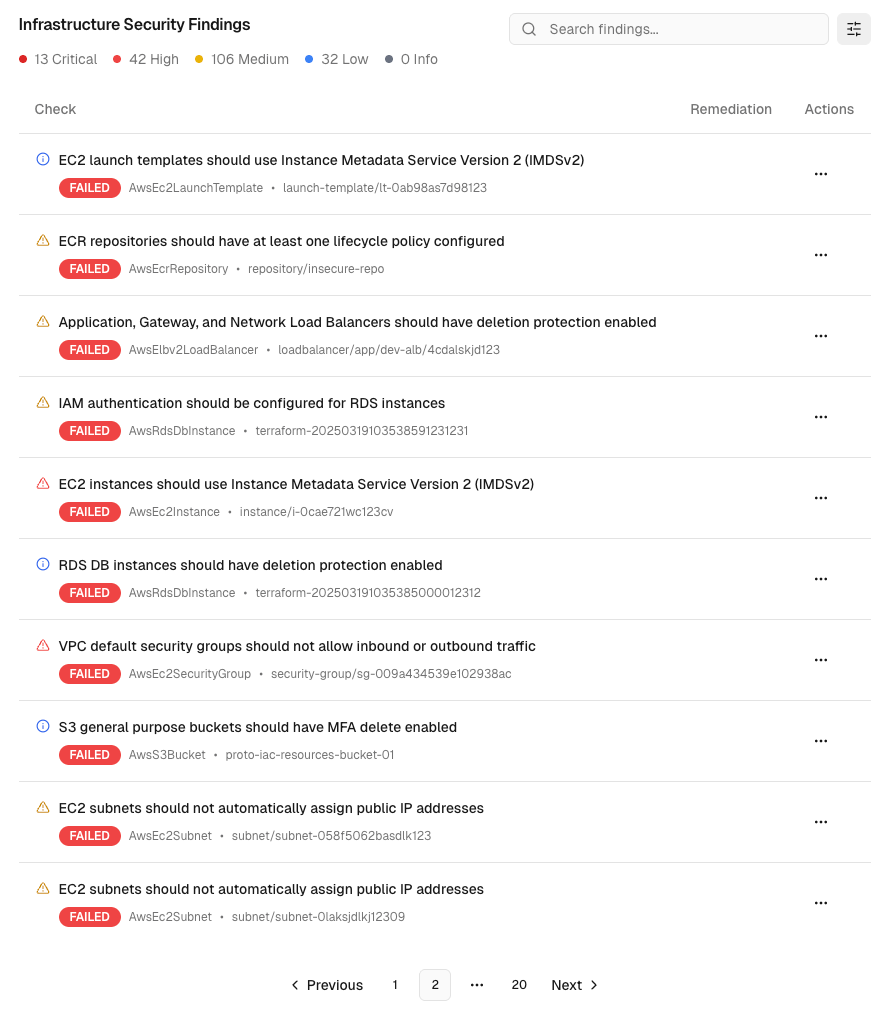
Search and Filtering
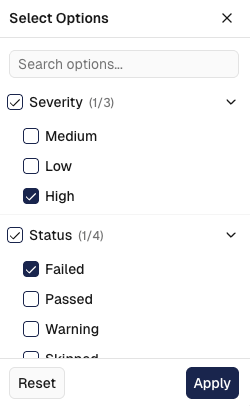
- Text Search: Search across finding descriptions, resource names, and security details
- Severity Filtering: Filter by Critical, High, Medium, Low, or Info severity levels
- Status Filtering: Show only specific finding states
Individual Finding Analysis
Click on any security finding to access detailed information and remediation guidance: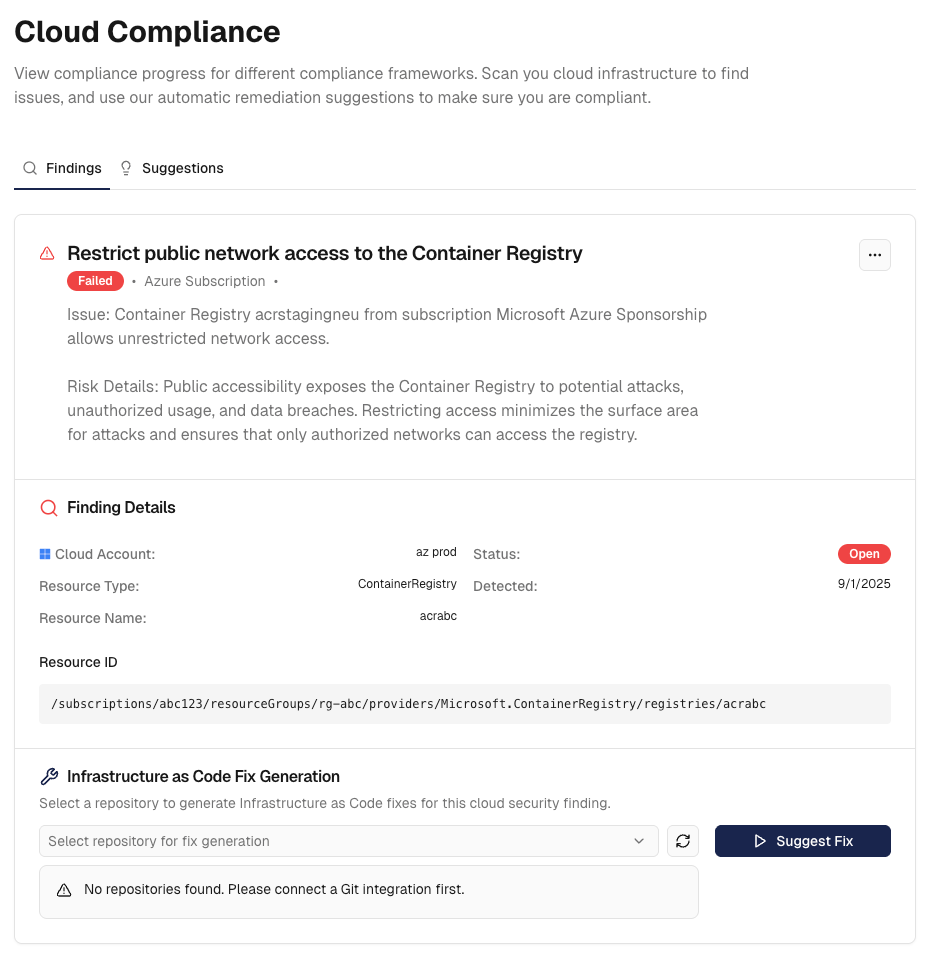
Finding Overview
Comprehensive Finding Information
- Finding Title and Description: Clear explanation of the identified security issue - Severity Assessment: Risk level with detailed impact analysis - Resource Context: Detailed information about affected cloud resources - Security Impact: Understanding of potential risks and vulnerabilities - Discovery Date: When the issue was detected by your security tools - Provider-Specific Details: Cloud provider context
AI-Powered Remediation Engine
Cloudgeni offers advanced AI-driven remediation capabilities through IaC:Intelligent Fix Generation
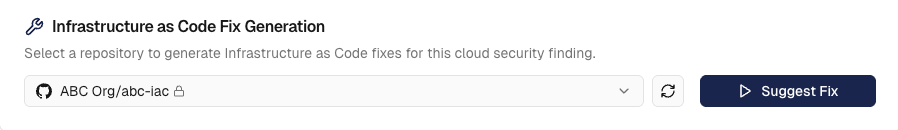
- From any finding detail page, click “Suggest Fix” to access AI-powered remediation
- Select your target repository where infrastructure-as-code fixes should be applied
- Cloudgeni’s AI engine analyzes the finding context and generates:
- Infrastructure as Code fixes (Terraform, Terragrunt, Azure Bicep)
- Policy and configuration updates for improved security posture
- Automated Validation to validate and fix IaC errors against your cloud environment
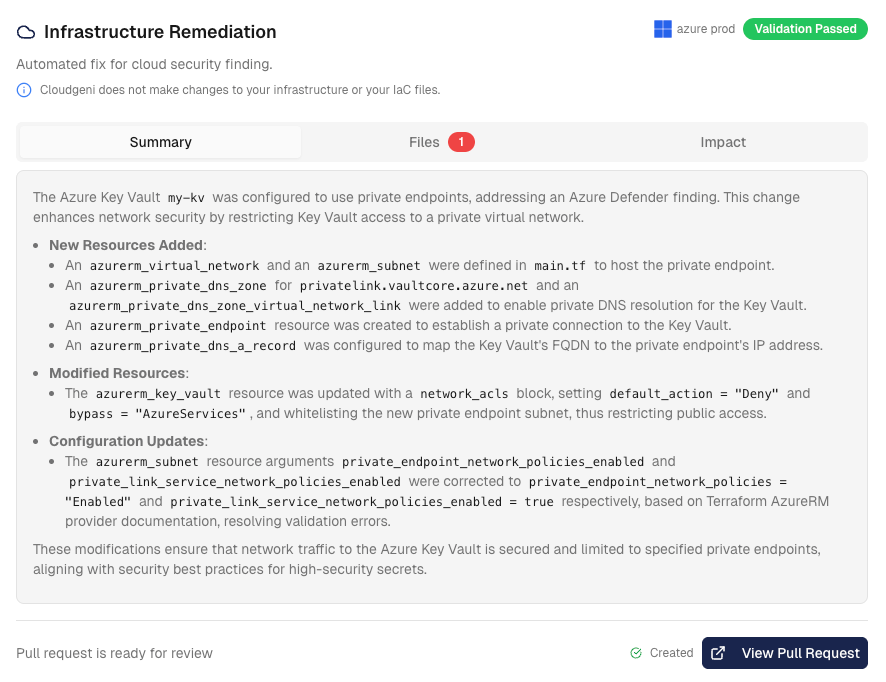
Remediation Tracking and Management
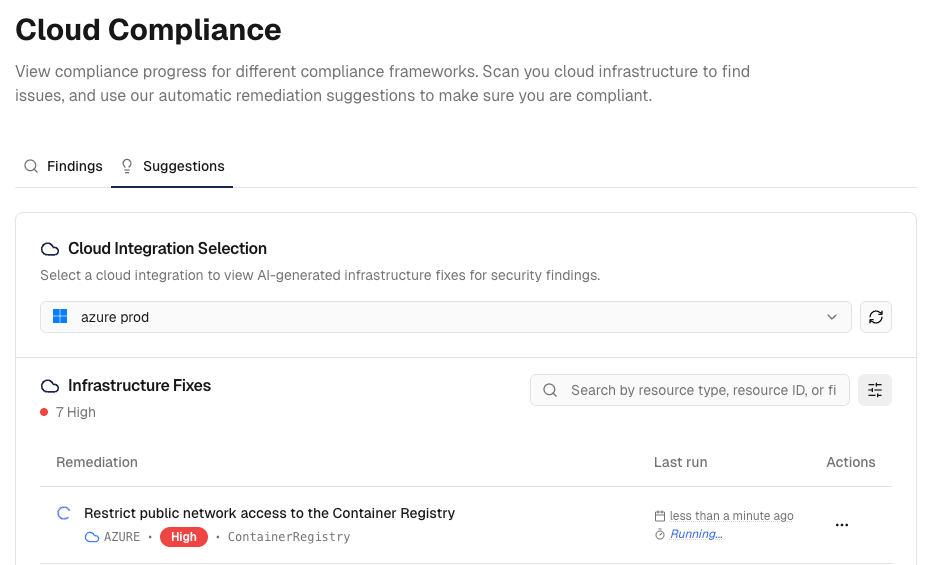
Comprehensive Remediation Management
- Active Remediations: In-progress fixes with real-time status tracking - Completed Implementations: Successfully created fixes with validation results - Failed Attempts: Issues requiring attention with error analysis and retry options - Pull Request Integration: Direct links to generated infrastructure-as-code fixes - Validation Results: Automated validation outcomes for proposed changes - Impact Assessment: Business impact analysis for each remediation
Cloud Monitors continuously evolves with enhanced security analysis and expanded cloud provider
coverage. The integration pulls the latest findings from your existing security tools to ensure
you always have up-to-date visibility into your security posture.