What Static Analysis Provides
- Comprehensive IaC security scanning for Terraform. - Security vulnerability detection in infrastructure configurations - AI-powered remediation suggestions with cloud validation - File-level code analysis showing exact locations and affected code snippets - Severity-based finding prioritization (Critical, High, Medium, Low, Info) - Real-time repository monitoring with automated scans on code changes
Infrastructure as Code Security
Static Analysis helps you implement security-first infrastructure development by catching issues early in the development cycle:Security Coverage
- Configuration Security: Detect misconfigured resources, insecure defaults, and dangerous settings - Access Control Issues: Identify overly permissive IAM policies, security group rules, and access configurations - Encryption Violations: Find unencrypted storage, databases, and data transmission configurations - Network Security: Detect insecure network configurations, open ports, and exposed resources - Compliance Standards: Check against security frameworks and industry best practices
Getting Started
Step 1: Connect Your Git Repository
Before running security analysis, you need to connect your Git repository containing Infrastructure as Code files.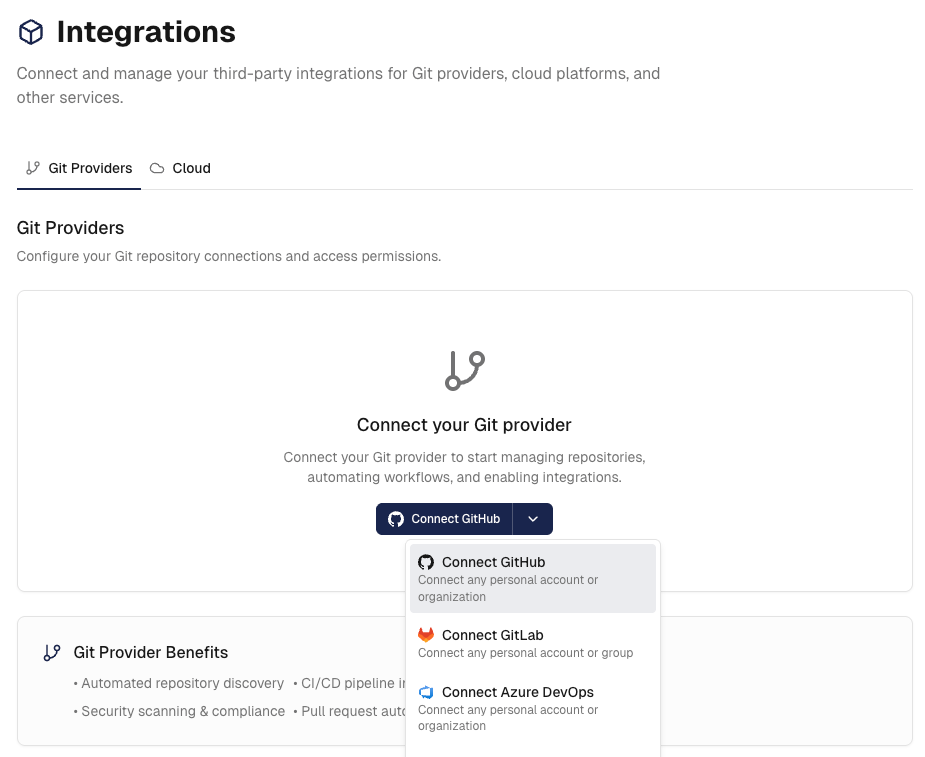
- Navigate to
Settings→Integrations→Gitin your Cloudgeni dashboard - Select your Git provider and follow the setup procedure:
- Important: Ensure your repository contains supported IaC files (currently only supports Terraform)
Step 2: Run Your First Security Analysis
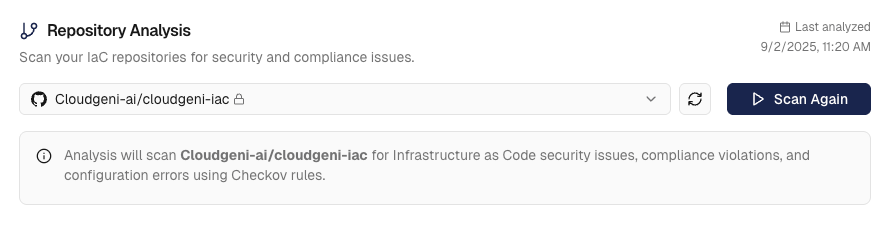
- Navigate to
Compliance→Static Analysisand select your repository - With your repository selected, click “Analyze” to start the security analysis
- The system will scan your IaC files for security issues (this usually takes less than 1 minute)
Understanding the Security Dashboard
Once your analysis completes, you’ll see a comprehensive dashboard with your IaC security findings: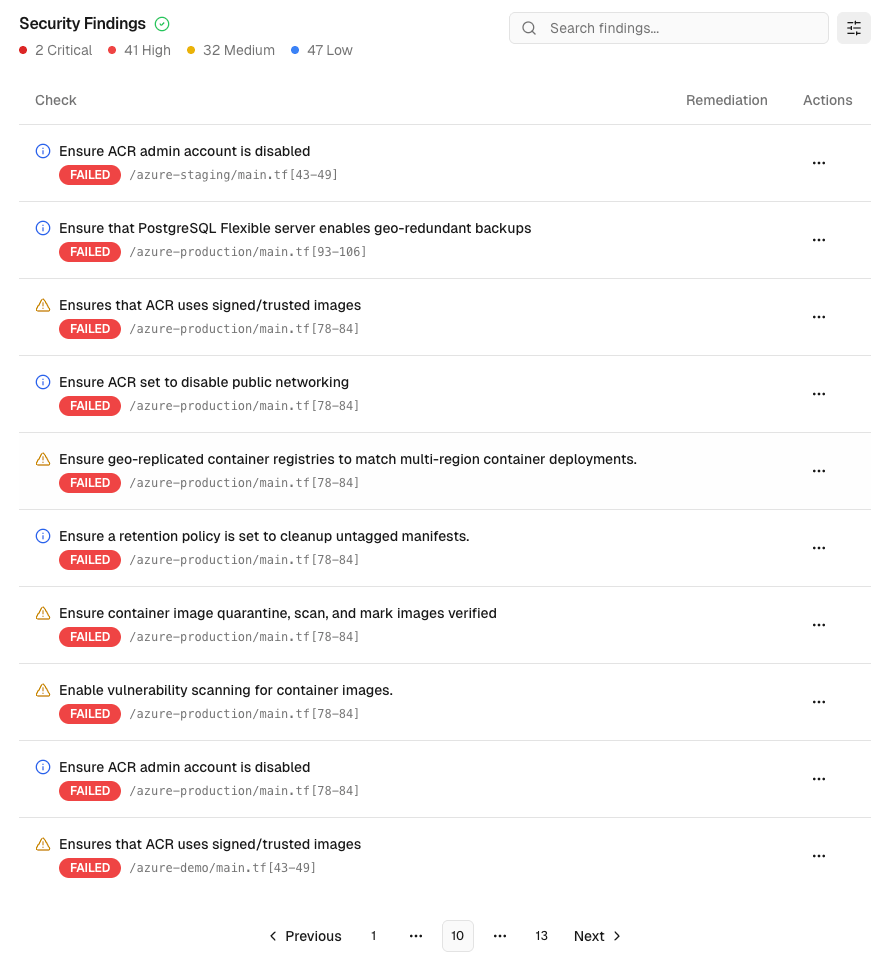
Search and Filtering
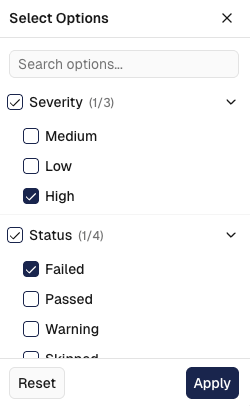
- Text Search: Search across finding descriptions, file paths, and security check details
- Severity Filtering: Filter by Critical, High, Medium, Low, or Info severity levels
- Check Result Filtering: Choose to show only FAILED or PASSED findings
Individual Finding Analysis
Click on any security finding to access detailed information and remediation guidance: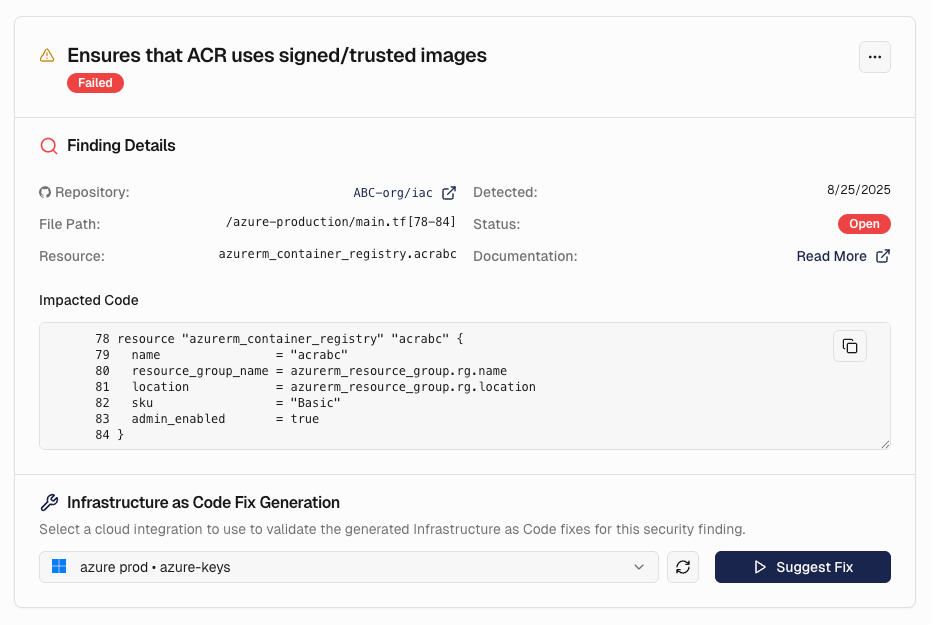
Comprehensive Finding Information
- Security Issue Details: Clear explanation of the configuration problem and its security impact - File Location: Exact file path and line numbers where the issue was detected - Affected Code: The specific IaC code snippet that contains the security issue - Check Documentation: Links to security guidelines and best practices for remediation - Detection Date: When the security issue was first identified
AI Agent for Infrastructure Remediation
- Click “Suggest Fix” to access AI-powered remediation for the specific security issue
- Select Cloud Integration: Choose which cloud account to use for validating the generated fixes
- Cloudgeni’s AI engine analyzes the security issue and generates:
- Secure IaC Code: Fixed Terraform code that resolves the security issue
- Cloud Validation: Tests the generated code against your actual environment to ensure it works
- Diff Analysis: Shows exactly what changes will be made to your infrastructure code
Remediation Management and Tracking
Navigate to the “Suggestions” tab to manage all your infrastructure remediation activities:Comprehensive Remediation Management
- Active Remediations: In-progress IaC fixes with real-time status tracking - Cloud Validation Status: See which fixes passed validation against your environment - Generated Code Diffs: Review proposed infrastructure changes before applying - Pull Request Integration: Direct links to generated infrastructure-as-code fixes - Validation Results: Detailed cloud validation outcomes with error explanations - Retry Failed Fixes: Re-attempt failed remediations with improved context
- Original Security Issue: Context about the vulnerability being fixed
- Generated Solution: The exact IaC code changes proposed by AI
- Cloud Validation Results: Whether the fix will work in your environment
- Implementation Status: Track progress from generation to pull request creation
Static Analysis continuously evolves with new security rules, expanded IaC framework support, and
enhanced remediation capabilities. The system automatically detects your Infrastructure as Code
frameworks and applies the appropriate security analysis.